基于源目标IP策略路由
发布时间:2015-06-17 12:09:57作者:知识屋
基于源目标IP策略路由
我们在写流量工程式的时候,可以用策略路由来做流量工量转发路径的控制。
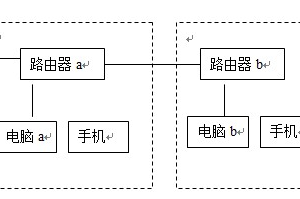
一。实验拓朴:

二。实验目的
1。学会灵活使用ACL 2。用策略路由使数据包走不同的数据线路传输 3。让R1的1.1.1.0/24走R2与R2的串行口 3。让数据包大于200字节的数据包走R2与R3的F0/0走。
www.zhishiwu.com
三。实验步骤
1。基本配置,R1 R2 R3配置IP地址,启用OSPF协议,在R1上建立四个网段用于测试用:1.1.1.0/24 1.1.2.0/24 1.1.3.0/24 1.1.4.0/24.
2。在R2上做策略路由
3。配置文档 只是一部分的配置,废话就不用发到上面了占地方,追求精,准,快
R1#show run
Building configuration...
Current configuration : 1110 bytes!
version 12.3!
ip cef
interface Loopback0
ip address 1.1.2.1 255.255.255.0 secondary 主要用于测试用。
ip address 1.1.3.1 255.255.255.0 secondary
ip address 1.1.4.1 255.255.255.0 secondary
ip address 1.1.1.1 255.255.255.0
ip ospf network point-to-point 指定为p2p网络类型,就不会出现/32的主机路由
!
interface Serial1/0
ip address 12.1.1.1 255.255.255.0
serial restart-delay 0
clock rate 64000
!
router ospf 10
router-id 1.1.1.1
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
!
R2#sh run
Building configuration..
interface Serial1/0
ip address 12.1.1.2 255.255.255.0
ip policy route-map tor3 一个接口下只能绑定一个route-map ,但可以通过顺序号建立多个条目
serial restart-delay 0
clock rate 64000
!
interface Serial1/1
ip address 23.1.1.2 255.255.255.0
serial restart-delay 0
clock rate 64000
router ospf 10
router-id 2.2.2.2
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
default-information originate always 一指一条默认路由到R1与R3的路由表中
O*E2 0.0.0.0/0 [110/1] via 12.1.1.2, 00:12:04, Serial1/0
!
ip classless
no ip http server
no ip http secure-server
!
!
access-list 1 permit 1.1.1.0 0.0.0.255 通过ACL控制那些数据采用策略路由转发
access-list 2 permit 1.1.4.0 0.0.0.255
!
route-map tor3 permit 1
match ip address 1 绑定ACL 1
set ip next-hop 23.1.1.3 下一次地址
!
route-map tor3 permit 2
match ip address 2
match length 200 300 基于数据包大小的条件大于200 小于300
set ip next-hop 213.1.1.3
!
www.zhishiwu.com
R3#sh run
Building configuration...
Current configuration : 1147 bytes
interface Loopback0
ip address 3.3.3.3 255.255.255.0
ip ospf network point-to-point
!
interface Serial1/0
ip address 23.1.1.3 255.255.255.0
serial restart-delay 0
clock rate 64000
router ospf 10
router-id 3.3.3.3
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
! www.zhishiwu.com
ip local policy route-map tor1 我们不能将策路路由绑定在接口上,因为路由器产生的数据包不会基于策略路由转发 所以要在全局下起用。ip local policy route-map tor1
route-map tor1 permit 10
match ip address 2
set ip next-hop 23.1.1.2
四。数据分析
1。在做完基本配置后,我们traceroute 3.3.3.3
R1# traceroute 3.3.3.3
Type escape sequence to abort.
Tracing the route to 3.3.3.3
1 12.1.1.2 524 msec 16 msec 164 msec
2 213.1.1.3 936 msec 704 msec 148 msec 可以看出我们的下一条不是23.1.1.3 而是F0/0出去的 www.zhishiwu.com
R1#ping 在这里就不讲扩展PING的命令格式了,用多了就知道了
Protocol [ip]:
Target IP address: 3.3.3.3
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface:
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]: re
Number of hops [ 9 ]:
Loose, Strict, Record, Timestamp, Verbose[RV]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet has IP options: Total option bytes= 39, padded length=40
Record route:
(12.1.1.1) 但要注意,我们现在traceroute ping 的源地址不是1.1.1.1,而是12.1.1.1
(213.1.1.2)
(3.3.3.3)
(213.1.1.3)
(12.1.1.2)
(12.1.1.1) <*>
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
End of list
www.zhishiwu.com
2。在R2做基于源IP的策略路由后,以下是R2 的debug ip policy
*Mar 31 19:13:08.183: IP: s=1.1.1.1 (Serial1/0), d=3.3.3.3, len 68, policy match
*Mar 31 19:13:08.183: IP: route map tor3, item 10, permit
*Mar 31 19:13:08.187: IP: s=1.1.1.1 (Serial1/0), d=3.3.3.3 (Serial1/1), len 68, policy routed
*Mar 31 19:13:08.187: IP: Serial1/0 to Serial1/1 23.1.1.3
3。在R3所有转发的数据包转发到set next-hop 23.1.1.2
*Mar 31 19:30:14.815: IP: s=3.3.3.3 (local), d=1.1.1.1, len 100, policy match
*Mar 31 19:30:14.819: IP: route map tor1, item 10, permit
*Mar 31 19:30:14.819: IP: s=3.3.3.3 (local), d=1.1.1.1 (FastEthernet0/0), len 100, policy routed
*Mar 31 19:30:14.819: IP: local to FastEthernet0/0 213.1.1.2
4.R1用1.1.4.0/24去PING R3,可以看到我们基于数据包大小的判定。
*Mar 31 20:09:07.755: IP: s=1.1.4.1 (Serial1/0), d=3.3.3.3, len 210, policy match
*Mar 31 20:09:07.755: IP: route map tor3, item 2, permit
*Mar 31 20:09:07.759: IP: s=1.1.4.1 (Serial1/0), d=3.3.3.3 (FastEthernet0/0), len 210, policy routed
*Mar 31 20:09:07.759: IP: Serial1/0 to FastEthernet0/0 213.1.1.3
www.zhishiwu.com
五:试验总结:
1。一个接口下只能配置一个策略条目,可以可这样
2#sh route-map
route-map tor3, permit, sequence 1 可以使用多个顺序号,默认以10为步进值。
Match clauses:
ip address (access-lists): 1
Set clauses:
ip next-hop 23.1.1.3
Policy routing matches: 3 packets, 210 bytes
route-map tor3, permit, sequence 2
Match clauses:
ip address (access-lists): 2
length 200 300
Set clauses:
ip next-hop 213.1.1.3
Policy routing matches: 13 packets, 2354 bytes
(免责声明:文章内容如涉及作品内容、版权和其它问题,请及时与我们联系,我们将在第一时间删除内容,文章内容仅供参考)
相关知识
-
怎么把无线路由器设置成无线交换机 TP-LINK无线路由器作为无线交换机教程
-
wifi无线路由没有信号怎么办 连接成功找不到无线路由器信号解决方法
-
如何利用WDS延伸wifi覆盖范围 路由器怎么开启WDS模式扩展WIFI范围
-

家用光纤路由器怎么设置步骤图解 光纤用户的路由器如何连接设置方法
-

无线路由器网络DNS被劫持了怎么办 如何查看路由器是否被劫持了方法
-
如何查看无线路由器有几个人用 怎么查询有多少人连接到我的路由器
-
使用宽带路由器设置过滤不良网站方法 如何利用路由器限制访问某些网站
-

路由器端口模块化和非模块化区别在哪 路由器分模块化和非模块化是什么意思
-

路由器和光猫ip地址冲突怎么办 路由器和光猫的区别是什么详细介绍
-
无线路由器固件损坏怎么修复方法 如何检测无线路由器是否损坏教程
软件推荐
更多 >-
1
 智能路由器哪个好 8款2015家用智能路由器推荐
智能路由器哪个好 8款2015家用智能路由器推荐2015-09-01
-
2
如何将WiFi信号隐藏防止别人用万能钥匙蹭网
-
3
路由器重置后怎么办 路由器重置后如何设置?
-
4
[WDS无线桥接功能] 教你如何扩展家中WIFI信号覆盖
-
5
192.168.1.1管理员密码是什么?
-
6
路由器怎么看宽带上网帐号和密码?查看路由器宽带密码方法图文介绍
-
7
极路由3怎么样?极路由3真机拆解评测
-
8
腾达A301怎么设置 腾达A301设置图文教程
-
9
水星路由器怎么设置无线网络密码?
-
10
腾达路由器怎么恢复出厂设置 Tenda路由器恢复出厂设置2种方法