Linux小脚本加固系统安全
发布时间:2013-03-05 18:32:20作者:知识屋
今天有朋友在Linux的群里喊需要写一个脚本,来实现对100多台Linux系统的统一安全配置,然后求助人来写这个脚本。我闲来无事,就接下来了。
都是非常基础的语法,没有做过优化,只是简单的实现了他提的要求,现在把脚本发下,如果有人愿意跟我一起改进或者有什么建议的请发站内信给我,大家一起讨论。
这个脚本最后有一点小问题,就是在追加审计策略的时候,脚本只能执行一次,如果执行两次,最后在策略追加时会报错,并且/etc/audit/audit.rules会不断增加,这个问题我后期会优化,使其执行多少次的结果都是一样的。
#!/bin/bash
DIR=/etc
#################################################################
##/etc/login.defs
##PASS_MAX_DAYS
echo "正在修改/etc/login.defs..."
sleep 1
max=`cat $DIR/login.defs |grep ^PASS_MAX_DAYS |awk '{print $2}'`
if [ $max != 90 ];then
sed -i '/^PASS_MAX_DAYS/s/'"$max"'/90/g' $DIR/login.defs
fi
##PASS_MIN_DAYS
min=`cat $DIR/login.defs |grep ^PASS_MIN_DAYS |awk '{print $2}'`
if [ $min != 0 ];then
sed -i '/^PASS_MIN_DAYS/s/'"$min"'/0/g' $DIR/login.defs
fi
##PASS_MIN_LEN
len=`cat $DIR/login.defs |grep ^PASS_MIN_LEN |awk '{print $2}'`
if [ $len != 8 ];then
sed -i '/^PASS_MIN_LEN/s/'"$len"'/8/g' $DIR/login.defs
fi
##PASS_WARN_AGE
warn=`cat $DIR/login.defs |grep ^PASS_WARN_AGE | awk '{print $2}'`
if [ $warn != 7 ];then
sed -i '/^PASS_WARN_AGE/s/'"$warn"'/7/g' $DIR/login.defs
fi
###########################################################
echo "正在修改用户组..."
sleep 1
sed -i 's/^uucp/#&/g' /etc/passwd
sed -i 's/^nuucp/#&/g' /etc/passwd
sed -i 's/^lp/#&/g' /etc/passwd
sed -i 's/^news/#&/g' /etc/passwd
sed -i 's/^games/#a&/g' /etc/passwd
sed -i 's/^uucp/#&/g' /etc/shadow
sed -i 's/^nuucp/#&/g' /etc/shadow
sed -i 's/^lp/#&/g' /etc/shadow
sed -i 's/^news/#&/g' /etc/shadow
sed -i 's/^games/#&/g' /etc/shadow
sed -i 's/^uucp/#&/g' /etc/group
sed -i 's/^nuucp/#&/g' /etc/group
sed -i 's/^lp/#&/g' /etc/group
sed -i 's/^news/#&/g' /etc/group
sed -i 's/^games/#&/g' /etc/group
###############################################
echo "正在修改禁止管理员远程登录..."
sed -i 's/^#PermitRootLogin yes/PermitRootLogin no/g' /etc/ssh/sshd_config
###############################################
echo "正在修改系统命令行保存条目..."
sleep 1
cat /etc/profile |grep ^HISTSIZE > /dev/null
if [ $? == 0 ];then
sed -i 's/^HISTSIZE=[0-9]{1,4}/HISTSIZE=30/g' /etc/profile
fi
cat /etc/profile |grep ^HISTFILESIZE > /dev/null
if [ $? == 1 ];then
echo "HISTFILESIZE=30" >> /etc/profile
fi
###############################################
echo "正在修改系统启动级别..."
sleep 1
init=`cat /etc/inittab |grep ^id |cut -d ":" -f 2`
if [ $init != 3 ];then
sed -i '/^id/s/'"${init}"'/3/g' /etc/inittab
fi
##############################################
echo "正在启用审计策略..."
echo "# Enable auditing" >> /etc/audit/audit.rules
echo "-e 1" >> /etc/audit/audit.rules
echo "## login configuration and information" >> /etc/audit/audit.rules
echo "-w /etc/login.defs -p wa -k CFG_login.defs" >> /etc/audit/audit.rules
echo "-w /etc/securetty -p wa -k CFG_securetty" >> /etc/audit/audit.rules
echo "-w /var/log/faillog -p wa -k LOG_faillog" >> /etc/audit/audit.rules
echo "-w /var/log/lastlog -p wa -k LOG_lastlog" >> /etc/audit/audit.rules
echo "-w /var/log/tallylog -p wa -k LOG_tallylog" >> /etc/audit/audit.rules
echo " " >> /etc/audit/audit.rules
echo "## directory operations" >> /etc/audit/audit.rules
echo "#-a entry,always -S mkdir -S mkdirat -S rmdir" >> /etc/audit/audit.rules
echo " " >> /etc/audit/audit.rules.bak
echo " " >> /etc/audit/audit.rules
echo "## cron configuration & scheduled jobs" >> /etc/audit/audit.rules
echo "-w /etc/cron.allow -p wa -k CFG_cron.allow" >> /etc/audit/audit.rules
echo "-w /etc/cron.deny -p wa -k CFG_cron.deny" >> /etc/audit/audit.rules
echo "-w /etc/cron.d/ -p wa -k CFG_cron.d" >> /etc/audit/audit.rules
echo "-w /etc/cron.daily/ -p wa -k CFG_cron.daily" >> /etc/audit/audit.rules
echo "-w /etc/cron.hourly/ -p wa -k CFG_cron.hourly" >> /etc/audit/audit.rules
echo "-w /etc/cron.monthly/ -p wa -k CFG_cron.monthly" >> /etc/audit/audit.rules
echo "-w /etc/cron.weekly/ -p wa -k CFG_cron.weekly" >> /etc/audit/audit.rules
echo "-w /etc/crontab -p wa -k CFG_crontab" >> /etc/audit/audit.rules
echo "-w /var/spool/cron/root -k CFG_crontab_root" >> /etc/audit/audit.rules
echo " " >> /etc/audit/audit.rules
echo " " >> /etc/audit/audit.rules
echo "## user, group, password databases" >> /etc/audit/audit.rules
echo "-w /etc/group -p wa -k CFG_group" >> /etc/audit/audit.rules
echo "-w /etc/passwd -p wa -k CFG_passwd" >> /etc/audit/audit.rules
echo "-w /etc/gshadow -k CFG_gshadow" >> /etc/audit/audit.rules
echo "-w /etc/shadow -k CFG_shadow" >> /etc/audit/audit.rules
echo "-w /etc/security/opasswd -k CFG_opasswd" >> /etc/audit/audit.rules
echo " " >> /etc/audit/audit.rules
echo "# ----- File System audit rules -----" >> /etc/audit/audit.rules
echo "正在重启审计服务..."
/sbin/service auditd restart
##################################################################
sleep 1
echo "脚本执行成功"
相关知识
-
linux一键安装web环境全攻略 在linux系统中怎么一键安装web环境方法
-
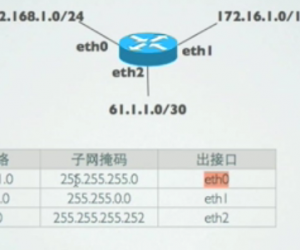
Linux网络基本网络配置方法介绍 如何配置Linux系统的网络方法
-
Linux下DNS服务器搭建详解 Linux下搭建DNS服务器和配置文件
-
对Linux进行详细的性能监控的方法 Linux 系统性能监控命令详解
-
linux系统root密码忘了怎么办 linux忘记root密码后找回密码的方法
-
Linux基本命令有哪些 Linux系统常用操作命令有哪些
-
Linux必学的网络操作命令 linux网络操作相关命令汇总
-
linux系统从入侵到提权的详细过程 linux入侵提权服务器方法技巧
-
linux系统怎么用命令切换用户登录 Linux切换用户的命令是什么
-
在linux中添加普通新用户登录 如何在Linux中添加一个新的用户
软件推荐
更多 >-
1
 专为国人订制!Linux Deepin新版发布
专为国人订制!Linux Deepin新版发布2012-07-10
-
2
CentOS 6.3安装(详细图解教程)
-
3
Linux怎么查看网卡驱动?Linux下查看网卡的驱动程序
-
4
centos修改主机名命令
-
5
Ubuntu或UbuntuKyKin14.04Unity桌面风格与Gnome桌面风格的切换
-
6
FEDORA 17中设置TIGERVNC远程访问
-
7
StartOS 5.0相关介绍,新型的Linux系统!
-
8
解决vSphere Client登录linux版vCenter失败
-
9
LINUX最新提权 Exploits Linux Kernel <= 2.6.37
-
10
nginx在网站中的7层转发功能