分享25个最好的SSH命令和技巧(英文)
发布时间:2014-09-05 17:24:17作者:知识屋
OpenSSH(Open Secure Shell)是使用SSH透过计算机网络加密通讯的实现。它是取代由SSH Communications Security所提供的商用版本的开放源代码方案。目前OpenSSH是OpenBSD的子计划。
下面列举了25个最好的SSH命令(英文原文):
1) Copy ssh keys to user@host to enable password-less ssh logins.
ssh-copy-id user@host
To generate the keys use the command ssh-keygen
2) Start a tunnel from some machine’s port 80 to your local post 2001
ssh -N -L2001:localhost:80 somemachine
Now you can acces the website by going to http://localhost:2001/
3) Output your microphone to a remote computer’s speaker
dd if=/dev/dsp | ssh -c arcfour -C username@host dd of=/dev/dsp
This will output the sound from your microphone port to the ssh target computer’s speaker port. The sound quality is very bad, so you will hear a lot of hissing.
4) Compare a remote file with a local file
ssh user@host cat /path/to/remotefile | diff /path/to/localfile -
Useful for checking if there are differences between local and remote files.
5) Mount folder/filesystem through SSH
sshfs name@server:/path/to/folder /path/to/mount/point
Install SSHFS from http://fuse.sourceforge.net/sshfs.html
Will allow you to mount a folder security over a network.
6) SSH connection through host in the middle
ssh -t reachable_host ssh unreachable_host
Unreachable_host is unavailable from local network, but it’s available from reachable_host’s network. This command creates a connection to unreachable_host through “hidden” connection to reachable_host.
7) Copy your SSH public key on a remote machine for passwordless login – the easy way
ssh-copy-id username@hostname
8) Directly ssh to host B that is only accessible through host A
ssh -t hostA ssh hostB
Of course you need to be able to access host A for this ;-)
9) Create a persistent connection to a machine
ssh -MNf
Create a persistent SSH connection to the host in the background. Combine this with settings in your ~/.ssh/config:
Host host
ControlPath ~/.ssh/master-%r@%h:%p
ControlMaster no
All the SSH connections to the machine will then go through the persisten SSH socket. This is very useful if you are using SSH to synchronize files (using rsync/sftp/cvs/svn) on a regular basis because it won’t create a new socket each time to open an ssh connection.
10) Attach screen over ssh
ssh -t remote_host screen -r
Directly attach a remote screen session (saves a useless parent bash process)
11) Port Knocking!
knock
Knock on ports to open a port to a service (ssh for example) and knock again to close the port. You have to install knockd.
See example config file below.
[options]
logfile = /var/log/knockd.log
[openSSH]
sequence = 3000,4000,5000
seq_timeout = 5
command = /sbin/iptables -A INPUT -i eth0 -s %IP% -p tcp –dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 5000,4000,3000
seq_timeout = 5
command = /sbin/iptables -D INPUT -i eth0 -s %IP% -p tcp –dport 22 -j ACCEPT
tcpflags = syn
12) Remove a line in a text file. Useful to fix
ssh-keygen -R
In this case it’s better do to use the dedicated tool
13) Run complex remote shell cmds over ssh, without escaping quotes
ssh host -l user $(
Much simpler method. More portable version: ssh host -l user “`cat cmd.txt`”
14) Copy a MySQL Database to a new Server via SSH with one command
mysqldump –add-drop-table –extended-insert –force –log-error=error.log -uUSER -pPASS OLD_DB_NAME | ssh -C user@newhost “mysql -uUSER -pPASS NEW_DB_NAME”
Dumps a MySQL database over a compressed SSH tunnel and uses it as input to mysql – i think that is the fastest and best way to migrate a DB to a new server!
15) Remove a line in a text file. Useful to fix “ssh host key change” warnings
sed -i 8d ~/.ssh/known_hosts
16) Copy your ssh public key to a server from a machine that doesn’t have ssh-copy-id
cat ~/.ssh/id_rsa.pub | ssh user@machine “mkdir ~/.ssh; cat >> ~/.ssh/authorized_keys”
If you use Mac OS X or some other *nix variant that doesn’t come with ssh-copy-id, this one-liner will allow you to add your public key to a remote machine so you can subsequently ssh to that machine without a password.
17) Live ssh network throughput test
yes | pv | ssh $host “cat > /dev/null”
connects to host via ssh and displays the live transfer speed, directing all transferred data to /dev/null
needs pv installed
Debian: ‘apt-get install pv’
Fedora: ‘yum install pv’ (may need the ‘extras’ repository enabled)
18) How to establish a remote Gnu screen session that you can re-connect to
ssh -t user@some.domain.com /usr/bin/screen -xRR
Long before tabbed terminals existed, people have been using Gnu screen to open many shells in a single text terminal. Combined with ssh, it gives you the ability to have many open shells with a single remote connection using the above options. If you detach with “Ctrl-a d” or if the ssh session is accidentally terminated, all processes running in your remote shells remain undisturbed, ready for you to reconnect. Other useful screen commands are “Ctrl-a c” (open new shell) and “Ctrl-a a” (alternate between shells). Read this quick reference for more screen commands: http://aperiodic.net/screen/quick_reference
19) Resume scp of a big file
rsync –partial –progress –rsh=ssh $file_source $user@$host:$destination_file
It can resume a failed secure copy ( usefull when you transfer big files like db dumps through vpn ) using rsync.
It requires rsync installed in both hosts.
rsync –partial –progress –rsh=ssh $file_source $user@$host:$destination_file local -> remote
or
rsync –partial –progress –rsh=ssh $user@$host:$remote_file $destination_file remote -> local
20) Analyze traffic remotely over ssh w/ wireshark
ssh root@server.com ‘tshark -f “port !22″ -w -’ | wireshark -k -i -
This captures traffic on a remote machine with tshark, sends the raw pcap data over the ssh link, and displays it in wireshark. Hitting ctrl+C will stop the capture and unfortunately close your wireshark window. This can be worked-around by passing -c # to tshark to only capture a certain # of packets, or redirecting the data through a named pipe rather than piping directly from ssh to wireshark. I recommend filtering as much as you can in the tshark command to conserve bandwidth. tshark can be replaced with tcpdump thusly:
ssh root@example.com tcpdump -w – ‘port !22′ | wireshark -k -i -
21) Have an ssh session open forever
autossh -M50000 -t server.example.com ‘screen -raAd mysession’
Open a ssh sess
相关知识
-
linux一键安装web环境全攻略 在linux系统中怎么一键安装web环境方法
-
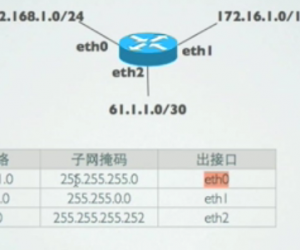
Linux网络基本网络配置方法介绍 如何配置Linux系统的网络方法
-
Linux下DNS服务器搭建详解 Linux下搭建DNS服务器和配置文件
-
对Linux进行详细的性能监控的方法 Linux 系统性能监控命令详解
-
linux系统root密码忘了怎么办 linux忘记root密码后找回密码的方法
-
Linux基本命令有哪些 Linux系统常用操作命令有哪些
-
Linux必学的网络操作命令 linux网络操作相关命令汇总
-
linux系统从入侵到提权的详细过程 linux入侵提权服务器方法技巧
-
linux系统怎么用命令切换用户登录 Linux切换用户的命令是什么
-
在linux中添加普通新用户登录 如何在Linux中添加一个新的用户
软件推荐
更多 >-
1
 专为国人订制!Linux Deepin新版发布
专为国人订制!Linux Deepin新版发布2012-07-10
-
2
CentOS 6.3安装(详细图解教程)
-
3
Linux怎么查看网卡驱动?Linux下查看网卡的驱动程序
-
4
centos修改主机名命令
-
5
Ubuntu或UbuntuKyKin14.04Unity桌面风格与Gnome桌面风格的切换
-
6
FEDORA 17中设置TIGERVNC远程访问
-
7
StartOS 5.0相关介绍,新型的Linux系统!
-
8
解决vSphere Client登录linux版vCenter失败
-
9
LINUX最新提权 Exploits Linux Kernel <= 2.6.37
-
10
nginx在网站中的7层转发功能