KailLinux渗透测试教程之Recon-NG框架
发布时间:2015-09-13 22:06:23作者:知识屋
Kail Linux渗透测试教程之Recon-NG框架
信息收集
信息收集是网络攻击最重要的阶段之一。要想进行渗透攻击,就需要收集目标的各类信息。收集到的信息越多,攻击成功的概率也就越大。本章将介绍信息收集的相关工具。Recon-NG框架
Recon-NG是由python编写的一个开源的Web侦查(信息收集)框架。Recon-ng框架是一个强大的工具,使用它可以自动的收集信息和网络侦查。下面将介绍使用Recon-NG侦查工具。启动Recon-NG框架,执行命令如下所示:
root@kali:~# recon-ng
_/_/_/ _/_/_/_/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/_/_/
_/ _/ _/ _/ _/ _/ _/_/ _/ _/_/ _/ _/
_/_/_/ _/_/_/ _/ _/ _/ _/ _/ _/ _/_/_/_/ _/ _/ _/ _/ _/_/_/
_/ _/ _/ _/ _/ _/ _/ _/_/ _/ _/_/ _/ _/
_/ _/ _/_/_/_/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/_/_/
+---------------------------------------------------------------------------+
| _ ___ _ __ |
| |_)| _ _|_ |_|.|| _ | _ |_ _ _ _ _ _|_o _ _ (_ _ _ _o_|_ |
| |_)|(_|(_|/ | ||||_/ _|_| || (_)| |||(_| | |(_)| | __)(/_(_|_|| | | // |
| / |
| Consulting | Research | Development | Training |
| http://www.blackhillsinfosec.com |
+---------------------------------------------------------------------------+
[recon-ng v4.1.4, Tim Tomes (@LaNMaSteR53)]
[56] Recon modules
[5] Reporting modules
[2] Exploitation modules
[2] Discovery modules
[1] Import modules
[recon-ng][default] >
以上输出信息显示了Recon-NG框架的基本信息。例如在Recon-NG框架下,包括56个侦查模块、5个报告模块、2个渗透攻击模块、2个发现模块和1个导入模块。看到[recon-ng][default] >提示符,表示成功登录Recon-NG框架。现在,就可以在[recon-ng][default] >提示符后面执行各种操作命令了。
首次使用Recon-NG框架之前,可以使用help命令查看所有可执行的命令。如下所示:
[recon-ng][default] > help
Commands (type [help|?]
---------------------------------
add Adds records to the database
back Exits current prompt level
del Deletes records from the database
exit Exits current prompt level
help Displays this menu
keys Manages framework API keys
load Loads specified module
pdb Starts a Python Debugger session
query Queries the database
record Records commands to a resource file
reload Reloads all modules
resource Executes commands from a resource file
search Searches available modules
set Sets module options
shell Executes shell commands
show Shows various framework items
spool Spools output to a file
unset Unsets module options
use Loads specified module
workspaces Manages workspaces
以上输出信息显示了在Recon-NG框架中可运行的命令。该框架和Metasploit框架类似,同样也支持很多模块。此时,可以使用show modules命令查看所有有效的模块列表。执行命令如下所示:
[recon-ng][default] > show modules
Discovery
---------
discovery/info_disclosure/cache_snoop
discovery/info_disclosure/interesting_files
Exploitation
------------
exploitation/injection/command_injector
exploitation/injection/xpath_bruter
Import
------
import/csv_file
Recon
-----
recon/companies-contacts/facebook
recon/companies-contacts/jigsaw
recon/companies-contacts/jigsaw/point_usage
recon/companies-contacts/jigsaw/purchase_contact
recon/companies-contacts/jigsaw/search_contacts
recon/companies-contacts/linkedin_auth
recon/contacts-contacts/mangle
recon/contacts-contacts/namechk
recon/contacts-contacts/rapportive
recon/contacts-creds/haveibeenpwned
……
recon/hosts-hosts/bing_ip
recon/hosts-hosts/ip_neighbor
recon/hosts-hosts/ipinfodb
recon/hosts-hosts/resolve
recon/hosts-hosts/reverse_resolve
recon/locations-locations/geocode
recon/locations-locations/reverse_geocode
recon/locations-pushpins/flickr
recon/locations-pushpins/picasa
recon/locations-pushpins/shodan
recon/locations-pushpins/twitter
recon/locations-pushpins/youtube
recon/netblocks-hosts/reverse_resolve
recon/netblocks-hosts/shodan_net
recon/netblocks-ports/census_2012
Reporting
---------
reporting/csv
reporting/html
reporting/list
reporting/pushpin
reporting/xml
[recon-ng][default] >
从输出的信息中,可以看到显示了五部分。每部分包括的模块数,在启动Recon-NG框架后可以看到。用户可以使用不同的模块,进行各种的信息收集。
【实例3-1】使用recon/domains-hosts/baidu_site模块,枚举baidu网站的子域。具体操作步骤如下所示:
(1)使用recon/domains-hosts/baidu_site模块。执行命令如下所示:
[recon-ng][default] > use recon/domains-hosts/baidu_site
(2)查看该模块下可配置选项参数。执行命令如下所示:
[recon-ng][default][baidu_site] > show options
Name Current Value Req Description
-------------- ---------------------- --------- --------------------------------------------------------
SOURCE default yes source of input (see 'show info' for details)
[recon-ng][default][baidu_site] >
从输出的信息中,可以看到有一个选项需要配置。
(3)配置SOURCE选项参数。执行命令如下所示:
[recon-ng][default][baidu_site] > set SOURCE baidu.com
SOURCE => baidu.com
从输出的信息中,可以看到SOURCE选项参数已经设置为baidu.com。
(4)启动信息收集。执行命令如下所示:
[recon-ng][default][baidu_site] > run
---------
BAIDU.COM
---------
[*] URL: http://www.baidu.com/s?pn=0&wd=site%3Abaidu.com
[*] map.baidu.com
[*] 123.baidu.com
[*] jingyan.baidu.com
[*] top.baidu.com
[*] www.baidu.com
[*] hi.baidu.com
[*] video.baidu.com
[*] pan.baidu.com
[*] zhidao.baidu.com
[*] Sleeping to avoid lockout...
-------
SUMMARY
-------
[*] 9 total (2 new) items found.
从输出的信息中,可以看到找到9个子域。枚举到的所有数据将被连接到Recon-NG放置的数据库中。这时候,用户可以创建一个报告查看被连接的数据。
【实例3-2】查看获取的数据。具体操作步骤如下所示:
(1)选择reporting/csv模块,执行命令如下所示:
[recon-ng][default] > use reporting/csv
(2)创建报告。执行命令如下所示:
[recon-ng][default][csv] > run
[*] 9 records added to '/root/.recon-ng/workspaces/default/results.csv'.
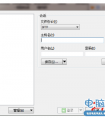
从输出的信息可以看到,枚举到的9个记录已被添加到/root/.recon-ng/workspaces/default/results.csv文件中。打开该文件,如图3.1所示。
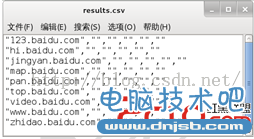
图3.1 results.csv文件
(3)从该界面可以看到,枚举到的所有子域。
用户也可以使用Dmitry命令,查询关于网站的信息。下面将介绍Dmitry命令的使用。
查看Dmitry命令的帮助信息。执行命令如下所示:
root@kali:~# dmitry -h
Deepmagic Information Gathering Tool
"There be some deep magic going on"
dmitry: invalid option -- 'h'
Usage: dmitry [-winsepfb] [-t 0-9] [-o %host.txt] host
-o Save output to %host.txt or to file specified by -o file
-i Perform a whois lookup on the IP address of a host
-w Perform a whois lookup on the domain name of a host
-n Retrieve Netcraft.com information on a host
-s Perform a search for possible subdomains
-e Perform a search for possible email addresses
-p Perform a TCP port scan on a host
* -f Perform a TCP port scan on a host showing output reporting filtered ports
* -b Read in the banner received from the scanned port
* -t 0-9 Set the TTL in seconds when scanning a TCP port ( Default 2 )
*Requires the -p flagged to be passed
以上信息显示了dmitry命令的语法格式和所有可用参数。下面使用dmitry命令的-s选项,查询合理的子域。执行命令如下所示:
root@kali:~# dmitry -s google.com
Deepmagic Information Gathering Tool
"There be some deep magic going on"
HostIP:173.194.127.71
HostName:google.com
Gathered Subdomain information for google.com
---------------------------------
Searching Google.com:80...
HostName:www.google.com
HostIP:173.194.127.51
Searching Altavista.com:80...
Found 1 possible subdomain(s) for host google.com, Searched 0 pages containing 0 results
All scans completed, exiting
从输出的信息中,可以看到搜索到一个子域。该子域名为www.google.com,IP地址为173.194.127.51。该命令默认是从google.com网站搜索,如果不能连接google.com网站的话,执行以上命令将会出现Unable to connect: Socket Connect Error错误信息。
相关知识
-
linux一键安装web环境全攻略 在linux系统中怎么一键安装web环境方法
-
Linux网络基本网络配置方法介绍 如何配置Linux系统的网络方法
-
Linux下DNS服务器搭建详解 Linux下搭建DNS服务器和配置文件
-
对Linux进行详细的性能监控的方法 Linux 系统性能监控命令详解
-
linux系统root密码忘了怎么办 linux忘记root密码后找回密码的方法
-
Linux基本命令有哪些 Linux系统常用操作命令有哪些
-
Linux必学的网络操作命令 linux网络操作相关命令汇总
-
linux系统从入侵到提权的详细过程 linux入侵提权服务器方法技巧
-
linux系统怎么用命令切换用户登录 Linux切换用户的命令是什么
-
在linux中添加普通新用户登录 如何在Linux中添加一个新的用户
软件推荐
更多 >-
1
 专为国人订制!Linux Deepin新版发布
专为国人订制!Linux Deepin新版发布2012-07-10
-
2
CentOS 6.3安装(详细图解教程)
-
3
Linux怎么查看网卡驱动?Linux下查看网卡的驱动程序
-
4
centos修改主机名命令
-
5
Ubuntu或UbuntuKyKin14.04Unity桌面风格与Gnome桌面风格的切换
-
6
FEDORA 17中设置TIGERVNC远程访问
-
7
StartOS 5.0相关介绍,新型的Linux系统!
-
8
解决vSphere Client登录linux版vCenter失败
-
9
LINUX最新提权 Exploits Linux Kernel <= 2.6.37
-
10
nginx在网站中的7层转发功能